The main issue of Internet link provided by Coffee shop (Public network) is that everyone can access the Access Point (AP)
* Web
You might know it is best to access a website with HTTPS (Hypertext Transfer Protocol Secure) instead of HTTP. But how?
For Chrome browser: "Use HTTPS"
https://chrome.google.com/extensions/detail/kbkgnojednemejclpggpnhlhlhkmfidi
For Firefox browser: "HTTPS Everywhere"
https://addons.mozilla.org/en-US/firefox/addon/229918/
It is also important to know that Facebook offers https access, so installing the "force https" when accessing facebook.com will let you enjoy a more secure web browsing experience.
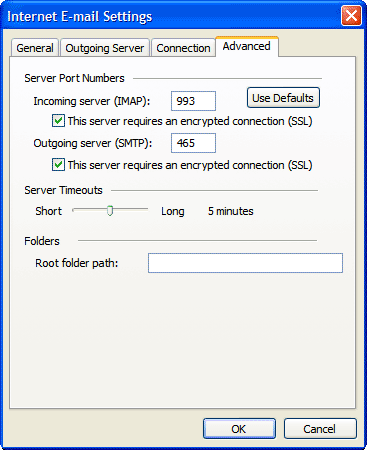
Email is one of the oldest product since Internet was invented. All messages are sent via plain text, which obviously not suitable for today's security standard. Therefore, it is necessary to further enhance the security by introducing Transport Layer Security (TLS). The network ports used are listed as below
- TCP 465 SMTP over TLS/SSL
- TCP 587 SMTP over TLS/SSLSTART
- TCP 993 IMAP over TLS/SSL
- TCP 995 POP3 over TLS/SSL
# Pictures are provided by mail.google.com
If we take Gmail as an example, we can find the setting is easy to make.
Related material: Enhancing security at Coffee Shop (A)
http://infosecmatrix.blogspot.com/2010/12/enhancing-security-at-coffee-shop.html